ISO 27001 defines the requirements for an Information Security Management System (ISMS). This defines a continuous improvement process (CIP, see Link) which enables the company to determine the necessary security measures in a risk-oriented approach and subsequently to implement and continuously improve them. Often an ISMS is perceived as a software tool, which it is not. The ISMS is a methodology and procedure that does not necessarily require a software tool in the first step. In larger companies, of course, software can support this methodology, especially if several departments or people are involved in the operation of the ISMS.
What are the most common motivations for ISO 27001 certification?
1) The competitive advantage
Using a 27001 certification for marketing and sales as an argument to customers that the company has a proven track record of adhering to recognized standards in the area of information security.
2) Liability of the company management
Implementing and certifying an IS management system can reduce management’s personal liability by avoiding organizational culpability.
3) The role for customers of the company and implementation of state of the art.
The company’s customers can use ISO 27001 certification as guarantees under the Article 28 of the GDPR (Processors) and Article 32 (Data Security Measures), among others.
4) Advantages or benefits for the company
Proof that security is taken care of and that this is confirmed by an independent body (the certifier).
5) Advantage for the management
Proof that management is taking care of business-critical tasks such as IT security.
The implementation of ISO 27001 enables a company to achieve and maintain an appropriate level of security. This particularly requires management support (often referred to as management commitment) and a willingness not only to write this method down, but also to actively integrate it into business processes.
The cost-effective alternative
Some companies use an approach based on the methodology and requirements of ISO 27001, but without performing the final certification. In this approach, the company relies on internationally recognized methods and standards. In this case, implementation is achieved in many areas in accordance with the current state of the art.
Does the new Network and Information Systems Security Act (NISG) affect me and does it require ISO 27001 certification?
The NISG (https://www.ris.bka.gv.at/Dokumente/BgblAuth/BGBLA_2018_I_111/BGBLA_2018_I_111.html) only concerns defined sectors defined in §2 of the Act:
Energy, transport, banking, financial market infrastructures, healthcare, drinking water supply, digital infrastructures as operators of essential services. In addition, providers of digital services, such as online marketplaces, online search engines and cloud computing services, as well as public administration bodies.
Whether a company must comply with the requirements of the Network and Information Systems Security Act as an operator of essential services will be determined by the Chancellor and is expected to be sent to the affected companies starting in early Q2 2019.
As a provider of digital services, you have to take action yourself and check whether the requirements of the NISG have to be met.
For operators of essential services in Austria, there is no ISO 27001 certification obligation, but there is an obligation in the specified divisions of
- Goverance and risk management
- Dealing with suppliers and third parties
- Security architecture
- System administration
- Identity and access management
- System maintenance and operations
- Physical security
- Incident detection
- Incident management
- Operational continuity
- Crisis management
to implement appropriate measures and to provide evidence of operational effectiveness through regular audits within a period of 3 years.
Although there is no ISO 27001 certification requirement, we believe it is essential to establish a structured approach. The mapping of the divisions with the requirements of ISO 27001 is recommended here. In conclusion, the use of ISO 27001 is sensible and recommended, as the CIP process can be used for the NISG evidence.
How important is the implementation of an ISMS system according to ISO 27001 for suppliers of large customers?
As a supplier of large customers, e.g. for the automotive industry, energy industry or pharmaceutical industry, it is almost indispensable to be able to prove that appropriate measures for the protection of information and personal data have been implemented. Large customers often already demand ISO 27001 certification as a minimum requirement from their suppliers. This may not yet have a direct impact on current contracts, but it is expected that ISO 27001 certification will be mandatory for suppliers in the future. The companies are therefore well advised to deal with an ISMS implementation and the ISO 27001 topic at an early stage and to plan it carefully.
The clients see the following advantages in requiring a 27001 certification of their suppliers:
- Application of the certification as a guarantee in terms of DSGVO Article 28 — Processor.
- Increasing the trustworthiness of the supplier when processing sensitive information of a principal
- Reduction of effort in vendor management, as individual security requirements no longer have to be negotiated with the supplier
- Reduction of effort in supplier audits with regard to information security
- Higher rating in supplier selection for certified companies
Companies that are already planning to use ISO 27001 certification may already have a competitive advantage over vendors that cannot demonstrate a structured approach to their information security or are planning to do so.
Which other companies are already ISO 27001 certified?
In a survey conducted in February 2019, around 150 companies in Austria are certified to ISO/IEC 27001.
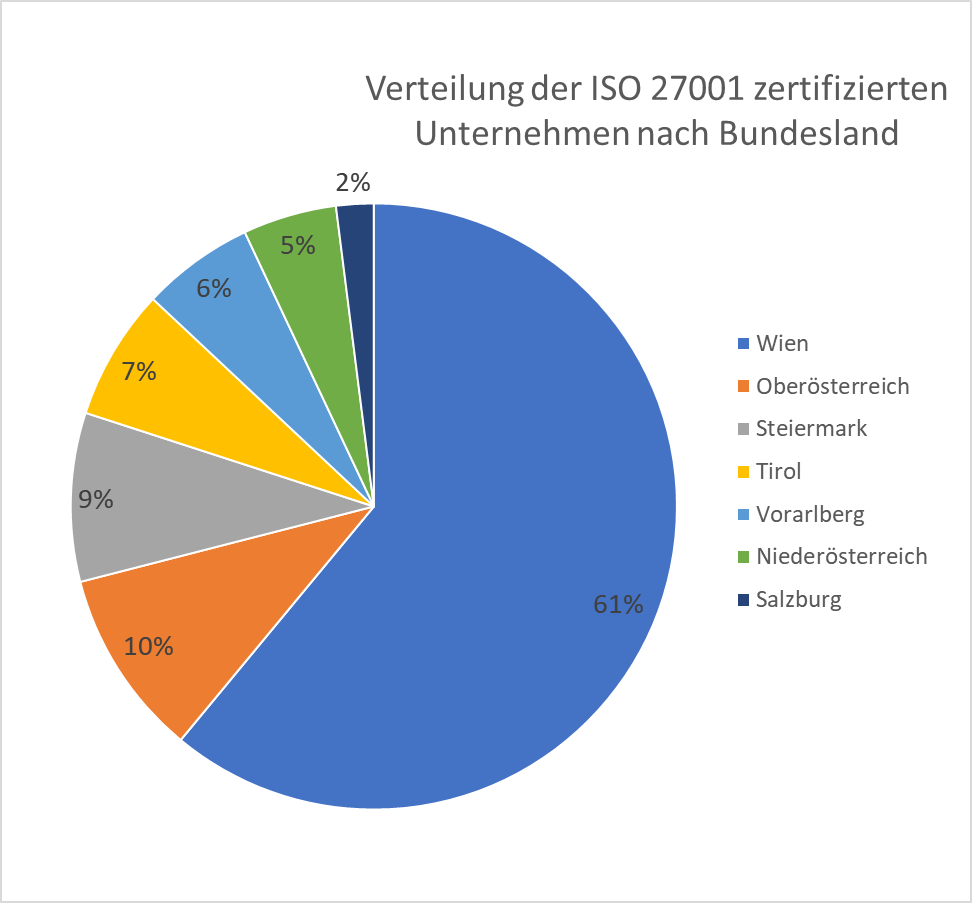
The top provinces with certified companies:
Vienna: 61% of ISO 27001 certified companies are from Vienna.
Upper Austria: 10%
Styria: 9%
Tyrol: 7%
Vorarlberg: 6%
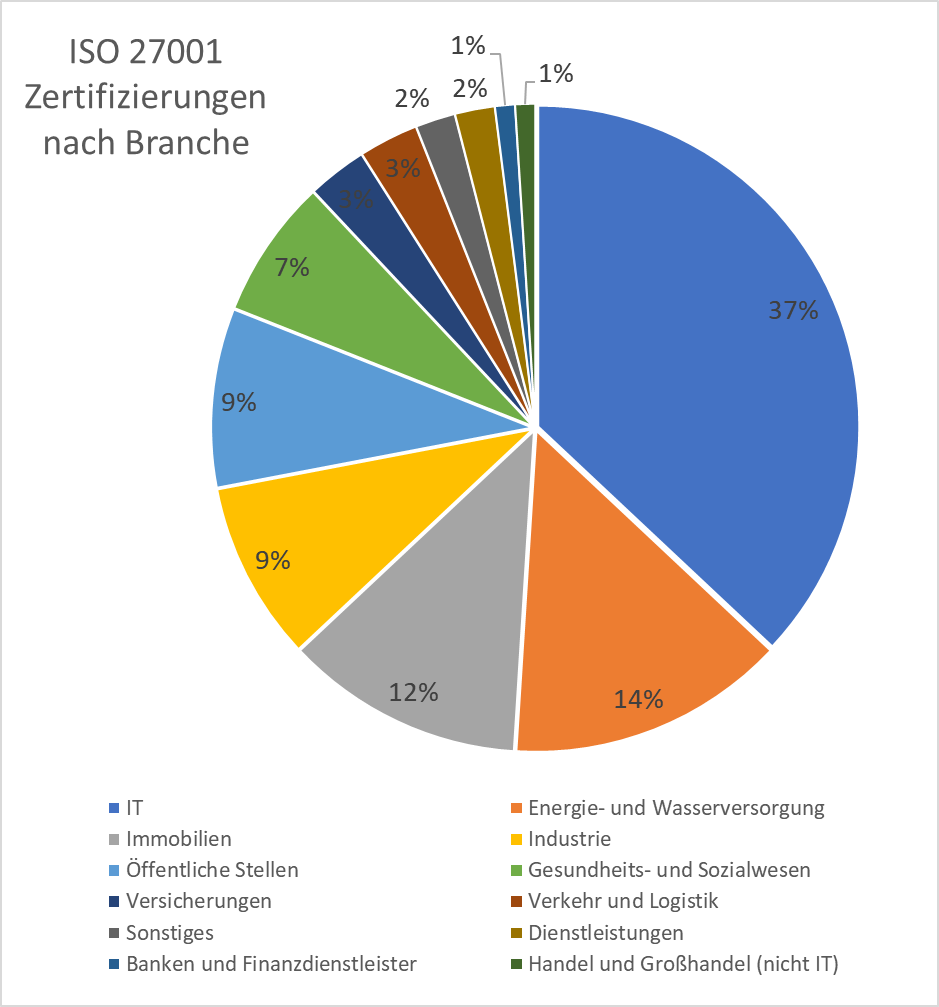
Among the industries, the IT sector dominates by a wide margin, with a number of data centers and Internet service providers having obtained ISO/IEC 27001 certification in recent years.
The top industries with ISO 27001 certification:
- IT: 37% of the ISO 27001 certified companies belong to the IT sector.
- Energy and water supply: 14%
- Real estate: 12
- Industry: 9%
- Public sector: 9%
- Health and social services: 7%
The number of ISO 27001 certified companies in Austria is significantly lower than the average in other countries such as Germany. One reason for this may be that operators of critical infrastructures have to prove ISO 27001 certification according to the IT Security Act 2016 (comparable to the Austrian NISG of 2018) and this is not the case in Austria. There are only selected accredited certification companies, the essential work lies in the structured support of the certification.
For this we will give tips for a successful start of a certification in one of the next articles.