ISMS Blog — Information Security — ISO/IEC 27001 — VDA ISA / TISAX — Examples — Guides — Checklists — Tips + Tricks
SEC4YOU ISMS Blog — valuable tips for your ISO/IEC 27001 project and certification, of course, also customers with the desire to improve security in the long term:
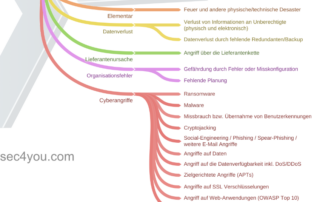
Information security risk survey for 27001 and TISAX®
Due to the rapidly increasing threats to an IT operation, every company should survey and evaluate the relevant IT threats with regard to information security. However, the selection of threats for the primary InfoSec protection goals confidentiality, integrity and availability is very complex, because there are no simple threat lists, especially for small and medium-sized enterprises. SEC4YOU has taken […]
free ISMS graphic: Delivery encrypted or locked
“Delivery encrypted or locked” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Abbildung: Lieferung verschlüsselt oder versperrt With this pictogram you can create understandable user policies, which are required for an ISMS according to […]
11 tips for fast ISO 27001 certification
We would like to provide valuable tips for the implementation of ISO 27001 for all companies that are aiming for certification. The ISO 27001 standard describes the requirements of an information security management system (ISMS), which also includes having a person responsible for information security. This person is often called the information security officer or chief information security officer […]
The new ISO/IEC 27002:2021
On the occasion of the SEC4YOU user meeting in June 2021, we presented the current draft the new ISO/IEC 27002:2021. The new ISO 27002:2021 is an extension of the aging ISO 27002:2013 (+corrections from 2014 and 2015) and adds the following control objectives: Threat intelligence Information security for use of cloud services ICT readiness for business continuity Physical security […]
free ISMS graphic: Shredder Security Level P5 — Document Shredder
“Shredder Security Level P5 — Document Shredder” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the function “Save graphic as” of your browser to use this pictogram for your information security system. Figure: Shredder safety level P5 With this pictogram you can create understandable user policies, which are required for an […]
free ISMS graphic: Shredder with control — document shredder
“Shredder with control — document shredder” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the function “Save graphic as” of your browser to use this pictogram for your information security system. Illustration: Shredder with control — document shredder. With this pictogram you can create understandable user policies, which are required for […]
free ISMS graphic: Shredder — Document shredder
“Shredder — Document Shredder” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the function “Save graphic as” of your browser to use this pictogram for your information security system. Figure: Shredder — Document Shredder With this pictogram you can create understandable user policies, which are required for an ISMS according to […]
free ISMS graphic: Mobile devices removable media encrypted
“Mobile devices removable media encrypted” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Mobile devices removable media encrypted With this pictogram you can create understandable user policies, which are required for an ISMS […]
free ISMS graphic: Mobile devices Removable media
“Mobile devices removable media” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Mobile devices Removable media With this pictogram you can create understandable user policies, which are required for an ISMS according to […]
free ISMS graphic: Delivery encrypted or locked with control
“Delivery encrypted or locked with control” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Delivery encrypted or locked with control With this pictogram you can create understandable user policies, which are required for […]
free ISMS graphic: Delivery
“Delivery” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the function “Save graphic as” of your browser to use this pictogram for your information security system. Figure: Delivery With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, e.g. the user policy […]
free ISMS graphic: Marking Strictly Confidential
“Marking Internal” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the function “Save graphic as” of your browser to use this pictogram for your information security system. Figure: Marking Strictly Confidential With this pictogram you can easily mark documents and create understandable user policies, which are required for an ISMS according […]
free ISMS graphic: Marking Internal
“Marking Internal” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the function “Save graphic as” of your browser to use this pictogram for your information security system. Figure: Marking Internal With this pictogram you can easily mark documents and create understandable user policies, which are required for an ISMS according to […]
free ISMS graphic: Labeling
“Labeling” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Abbildung: Klassifizierung With this pictogram you can easily mark documents and create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, […]
free ISMS graphic: Disposal with control or proof
“Disposal with control” — “Controlled disposal” — “Disposal with proof” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the function “Save graphic as” of your browser to use this pictogram for your information security system. Figure: Disposal control With this pictogram you can create understandable user policies, which are required for […]
free ISMS graphic: Disposal protected and locked
“Disposal protected and locked” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Disposal protected and locked With this pictogram you can create understandable user policies, which are required for an ISMS according to […]
free ISMS graphic: Disposal protected / Reisswolf
“Disposal protected” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Disposal protected With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, e.g. the […]
free ISMS graphic: Disposal
“Disposal” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Disposal With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, e.g. the user policy […]
free ISMS graphic: Email Encryption and Control
“Email Encryption and Control” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Email encryption control With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC […]
free ISMS graphic: Email encryption
“Email Encryption” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Email encryption With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, e.g. the […]
free ISMS graphic: Email control
“Email Transport Encryption” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Email transport encryption With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, […]
free ISMS graphic: Email control
“Email Control” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Email control With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, e.g. the […]
free ISMS graphic: Email Recipient Check
“Email Recipient Check” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Email recipient check With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, […]
free ISMS graphic: Two-factor authentication — 2FA
“Two-factor authentication — 2FA” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Two-factor authentication With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, […]
free ISMS graphic: Disclosure Control Authorization Data-Owner
“Disclosure Control Authorization Data-Owner” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Forwarding control authorization data owner With this pictogram you can create understandable user policies, which are required for an ISMS according […]
free ISMS graphic: Disclosure control authorization data owner
“Disclosure control authorization data owner” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Disclosure control authorization data owner With this pictogram you can create understandable user policies, which are required for an ISMS […]
free ISMS graphic: Confidentiality agreement — NDA personal
“Confidentiality agreement — NDA personal” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the function “Save graphic as” of your browser to use this pictogram for your information security system. Figure: Confidentiality agreement — NDA — personal With this pictogram you can create understandable user policies, which are required for an […]
free ISMS graphic: Confidentiality agreement — NDA with company
“Confidentiality agreement — NDA with company” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the function “Save graphic as” of your browser to use this pictogram for your information security system. Figure: Confidentiality agreement — NDA — Company With this pictogram you can create understandable user policies, which are required for […]
free ISMS graphic: Confidentiality agreement — NDA
“Confidentiality Agreement — NDA” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Confidentiality agreement — NDA With this pictogram you can create understandable user policies, which are required for an ISMS according to […]
free ISMS graphic: Forbidden
“Forbidden” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Forbidden With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, e.g. the user policy […]
free ISMS graphic: Cloud forbidden
“Cloud forbidden” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Cloud forbidden With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, e.g. the […]
free ISMS graphic: Cloud control
“Cloud control” or “controlled cloud” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Cloud control With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC […]
free ISMS graphic: Cloud allowed with 2FA
“Cloud allowed with 2FA” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Cloud allowed with 2FA With this pictogram you can create understandable user policies, which are required for an ISMS according to […]
free ISMS graphic: Cloud allowed
“Cloud allowed” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Cloud allowed With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, e.g. the […]
free ISMS graphic: Cloud with 2FA
“Cloud with 2FA” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Cloud with 2FA With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, […]
free ISMS graphic: Storage server encrypted with 2FA
“Storage server encrypted with 2FA” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Storage server encrypted 2FA With this pictogram you can create understandable user policies, which are required for an ISMS according […]
free ISMS graphic: Cloud
“Cloud” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Cloud With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, e.g. the user policy […]
free ISMS graphic: Storage Server
“Storage Server” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Storage Server With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, e.g. the […]
free ISMS graphic: Storage notebook encrypted — server encrypted with 2FA
“Storage notebook encrypted — server unencrypted with 2FA” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Storage notebook encrypted server encrypted with 2FA With this pictogram you can create understandable user policies, which […]
free ISMS graphic: Storage notebook encrypted — server encrypted
“Storage notebook encrypted — server encrypted” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Storage Notebook encrypted Server encrypted With this pictogram you can create understandable user policies, which are required for an […]
free ISMS graphic: Storage notebook encrypted — server unencrypted
“Storage notebook encrypted — server unencrypted” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Storage notebook encrypted — server unencrypted With this pictogram you can create understandable user policies, which are required for […]
free ISMS graphic: Permitted processing
“Permitted processing” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Allowed processing With this pictogram you can create understandable user policies, which are required for an ISMS according to ISO/IEC 27001, e.g. the […]
free ISMS graphic: Marking Internal
“Marking Internal” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Classification marking internal With this pictogram you can easily mark documents and create understandable user policies, which are required for an ISMS according […]
free ISMS graphic: Marking Restricted
“Marking Restricted” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Classification Marking Restricted With this pictogram you can easily mark documents and create understandable user policies, which are required for an ISMS according […]
free ISMS graphic: Labeling BSI very high / TISAX very high
“Marking very high” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Classification marking very high With this pictogram you can easily mark documents and create understandable user policies, which are required for an […]
free ISMS graphic: BSI high / TISAX high marking
“Marking high” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Classification Marking High With this pictogram you can easily mark documents and create understandable user policies, which are required for an ISMS according […]
free ISMS graphic: Strictly Confidential Marking
Marking “Confidential” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Pictogram — Confidential marking With this pictogram you can mark documents and at the same time create easy to understand user policies, which […]
free ISMS graphic: without marking — without classification
“Without labeling” — “without classification” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the function “Save graphic as” of your browser to use this pictogram for your information security system. Figure: Without marking — Without classification With this pictogram, you can create easy-to-understand user policies that are required for an ISMS […]
free ISMS graphic: Strictly Confidential Marking
Marking “Strictly Confidential” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Pictogram — Strictly Confidential With this pictogram you can mark documents and at the same time create easy to understand user policies, […]
free ISMS graphic: Marking Confidential
Marking “Confidential” — for your ISMS we are happy to provide our free and royalty-free graphic. Use the “Save graphic as” function of your browser to use this pictogram for your information security system. Figure: Pictogram: Classification Confidential With this pictogram you can mark documents and at the same time create easy to understand user policies, which are […]
Does the new Network and Information Systems Security Act (NISG) affect me and does it require ISO 27001 certification?
The Network and Information System Security Act — NISG (see publications) only concerns defined sectors defined in §2 of the Act: Energy, transport, banking, financial market infrastructures, healthcare, drinking water supply, digital infrastructures as operators of essential services. In addition, providers of digital services, such as online marketplaces, online search engines and cloud computing services, as well as public […]
Should I certify my company to ISO 27001?
ISO 27001 defines the requirements for an Information Security Management System (ISMS). This defines a continuous improvement process (CIP, see Link) which enables the company to determine the necessary security measures in a risk-oriented approach and subsequently to implement and continuously improve them. Often an ISMS is perceived as a software tool, which it is not. The ISMS is […]
Companies that want to be certified according to ISO/IEC 27001 or establish an ISMS according to 27001 face the challenges of creating guidelines, establishing processes and establishing a PDCA cycle as a continuous improvement process for information security.
Especially the definition and monitoring of KPIs within the ISMS is an important task of the CISO.
In this blog, SEC4YOU offers practice-proven assistance for the creation and optimization of information security management systems.