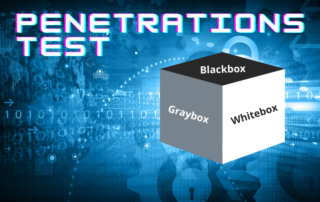
Comparison: Blackbox Test, Whitebox Test, Graybox Test
Before performing a penetration test, the question arises as to how the pentest should be performed. Here, pentesters distinguish between the following approaches: Blackbox test Whitebox test Graybox Text Which test is best suited for an audit? Black box or black box test With this penetration test method, the pentester does not [...]