Organizations that wish to certify to ISO/IEC 27001, or establish an ISMS to 27001, have the challenges of implementing the measures in Classification A.8.2 of Appendix A. In summary, these requirements are that:
- Information receives an appropriate level of protection according to its value;
- Information is classified according to external and internal requirements;
- information is labeled according to a classification scheme;
- there are procedures for handling it according to the classification scheme.
Reference English: A.8.2 Information classification, A.8.2.1 Classification of information, A.8.2.2 Labelling of information, A.8.2.3 Handling of assets
The classification of information
Past experience has shown us that the classic classification scheme of “Public”, “Internal”, “Confidential” and “Strictly Confidential” works poorly in practice, here is an overview of the scheme.
| Öffentlich | Intern | Vertraulich | Streng Vertraulich |
|---|---|---|---|
| Daten sind für jedermann, auch außerhalb der Firma, zugänglich. | Interne Daten werden lediglich den eigenen Mitarbeitern zugänglich gemacht. | Vertraulich definierte Daten sind lediglich einer begrenzten Anzahl an Mitarbeitern zugänglich, z.B. Personaldaten, Kundenlisten, Kalkulationen. | Streng vertrauliche Daten sind punktuell und ausschließlich bestimmten definierten Personen zugänglich. Eine Weitergabe kann das Unternehmen nachhaltig schädigen. |
The weaknesses of the classic classification scheme are:
- Employees are overwhelmed with labeling all documents; during an audit, the auditor finds tons of unlabeled “Internal” information.
- Employees do not understand the difference between “Public” and “Internal”.
- Particularly diligent employees quickly identify “Confidential” or “Strictly Confidential” information in their work documents, causing high effort and high costs in information handling.
Explanations to ISO/IEC 27001 Annex A — A.8.2 Information classification
Inherent in the goal of this control is the requirement that companies provide a level of protection for their information. It must be taken into account that different information has different values for the company. For example, employee data, customer data and development data typically require better protection than product information.
Explanation to A.8.2.1 Classification of information
With this measure, the standard aims to ensure that information is classified at all times, whereby the classification level must be derived from legal requirements, or value or criticality.
Explanation to A.8.2.2 Labeling of information
The purpose of labeling information is to enable users to easily identify the information classification level of the data in question. This labeling must cover electronically stored data as well as printed and archived information.
Explanation to A.8.2.3 Value handling
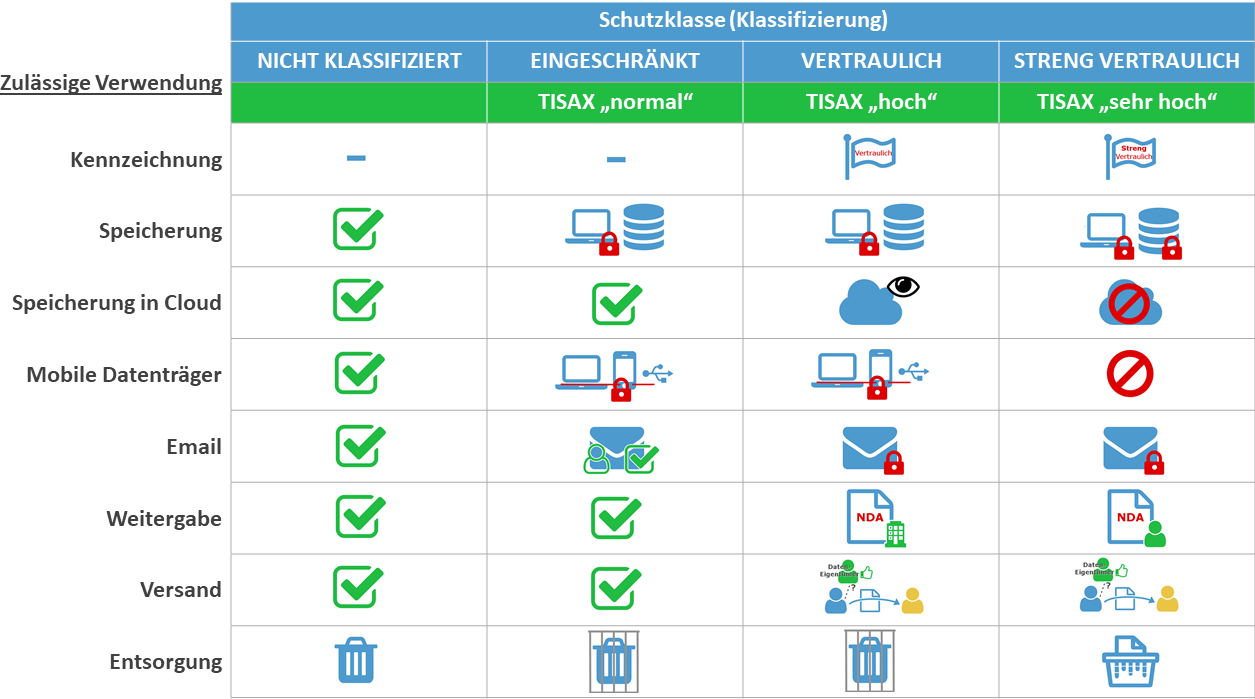
In addition to the labeling of information according to the information classification scheme, users need understandable instructions on how to handle the data. A matrix of the most important ways of handling information and where it can be stored has proven useful here:
- How to label?
- Where can the information be stored? (at the client, on which servers)
- May the information be stored in the cloud? (if yes, in which clouds)
- Is storage on mobile media or smartphone allowed?
- Are employees allowed to send classified information via email, if so with what additional protection methods?
- To whom and with what requirements may classified information be shared? (both electronically and in paper form).
- May information of the individual protection classes be sent? If so, from whom is authorization required?
- How must information be disposed of? Specifically, this includes paper documents and storage media.
All these points can be summarized in a matrix of permissible use. We recommend using meaningful pictograms here and are happy to provide the graphics developed by SEC4YOU.
In the Assignment table — Assignment of ISO/IEC27001 and ISO/IEC27002 to modernized IT-Grundschutz from the German BSI, you will find a reference to BSI Standard 200–2, Chapter 8.2 Determining the need for protection, on page 11:
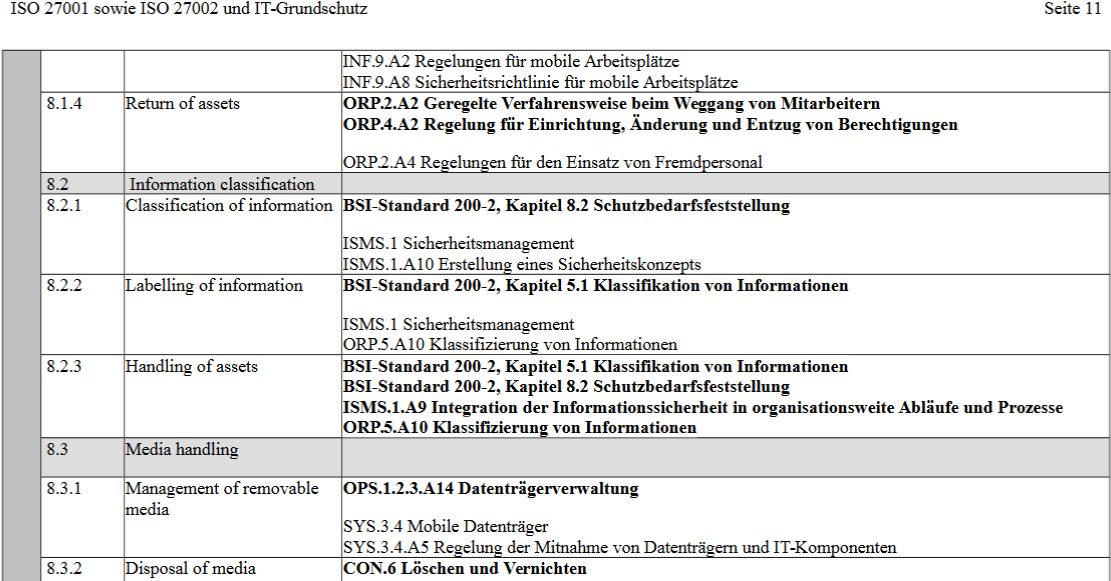
This protection needs assessment in BSI Standard 200–2 significantly simplifies the classification scheme by dispensing with the classes “Public” and “Internal” and instead recommends only three categories “Normal” as well as “High” and “Very High”.
| normal | hoch | sehr hoch |
|---|---|---|
| The damage effects are limited and manageable. | The damage impact can be significant. | The damage effects can reach existentially threatening, catastrophic proportions. |
The following advantages result from the BSI categories:
- The often incorrect use of the “Internal” classification is eliminated.
- The little information that is actually “Public” is not taken into account and simplifies the guideline.
- Due to the naming of catastrophic extent for the category “very high”, there are usually only a few information values of this protection category. This reduces costs for expensive technical measures.
The labeling of information
Especially with the classical classification scheme with “Public”, “Internal”, “Confidential” and “Strictly Confidential”, the marking of all four categories is a very complex task, especially since information is often also stored in non-office documents e.g. graphics, text files, databases.
Example of a policy for marking information:
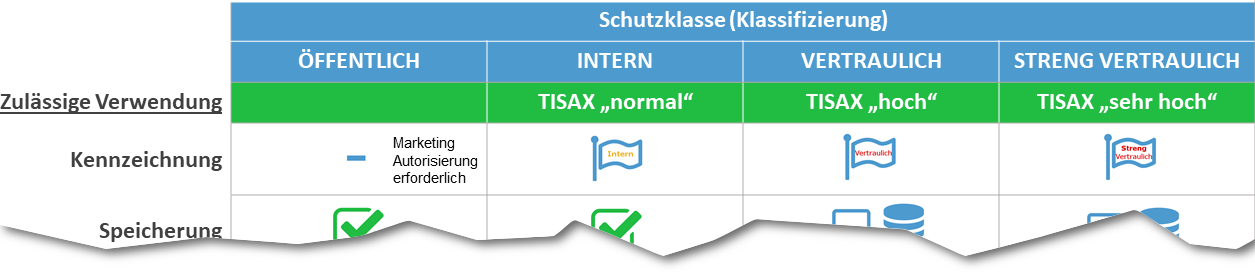
ISMS Tip: Do away with the classification categories “PUBLIC” and “INTERNAL”, which are confusing for users, and instead introduce the two categories “NOT CLASSIFIED” and “RESTRICTED” (or also “NORMAL”). Both protection classes can be introduced without the need to mark the documents.
The SEC4YOU recommendation, which is based on the BSI Standard 200–2, makes it possible to formulate this guideline in a much simpler way:
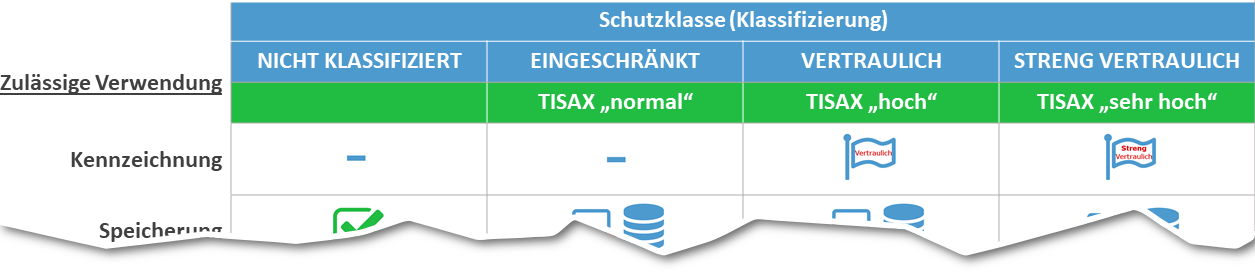
Appropriate classification of information values for TISAX certification
As you can see in the graphic, the BSI recommendation is identical to the VDA ISA recommendation for the Information security in the automotive industry. In the document Harmonization of Classification Levels, the German Association of the Automotive Industry (VDA) offers the following general protection classes for companies, depending on the potential damage: “normal”, “high” and “very high”. Automotive suppliers seeking TISAX certifications are well advised to implement the BSI = VDA ISA protection classes.
Recommendation: Describe in your policy that “internal” data or information of the protection class “normal” does not need to be marked. This is also a recommended action in the ISO/IEC 27002 standard, paragraph 8.2.2.
However, when implementing ISO/IEC 27001, it is important for the classifications “Confidential” as well as “Strictly Confidential” (or according to BSI “High” as well as “Very High”) that all classified documents are marked. This can be achieved with:
- Train your employees to create confidential documents.
- Special marked areas in the intranet with strict user restrictions
- Word, Excel and PowerPoint templates for confidential and strictly confidential data (or “high” and “very high”) on which the classification is clearly visible on each document page.
- For the “strictly confidential” or BSI “very high” class, the allowed recipients must be listed at the beginning of the document.
Important: When marking, take into account both electronically stored documents and paper printouts of these documents.
The handling of values
ISO/IEC 27001 is comparatively vague on the handling of information assets, but it requires:
“Procedures for handling assets are developed and implemented according to the information classification scheme used by the organization.”
In practice, organizations document and train employees on guidelines for the following handling methods:
- Labeling
- Storage
- Storage in the cloud
- Use of mobile devices and data carriers
- Email use
- Sharing
- Physical shipping
- Data destruction
Here is an example of a policy for handling information assets in the classic classification scheme:
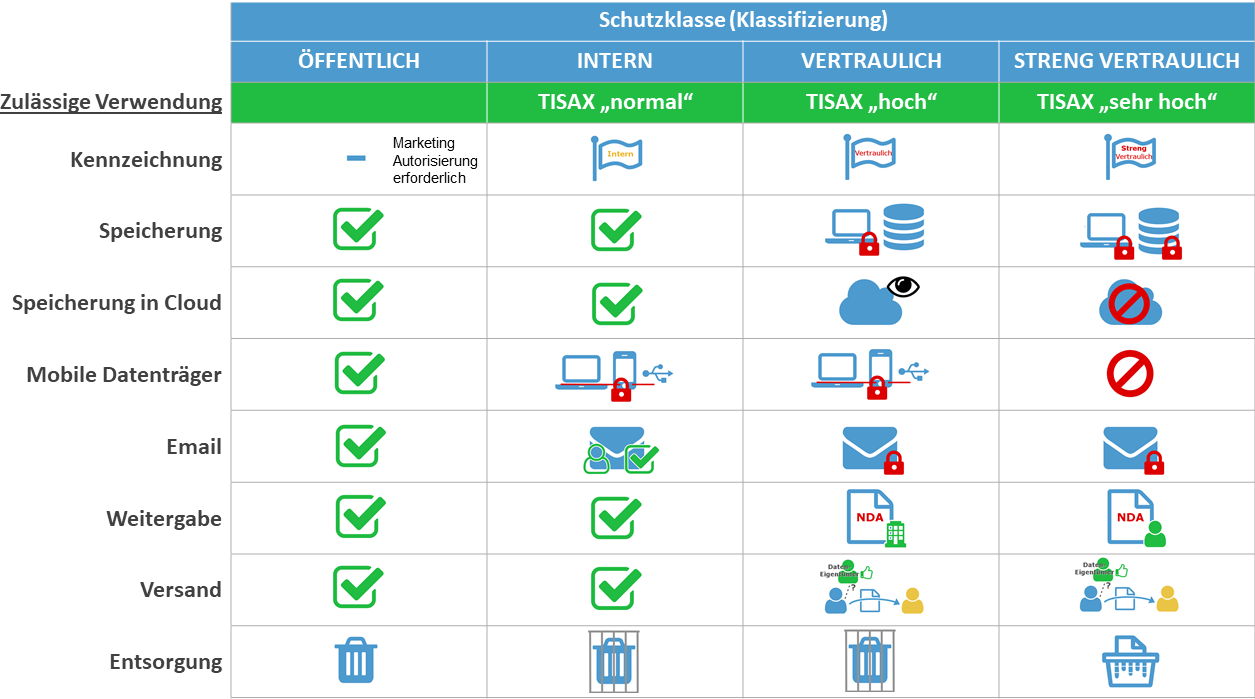
Handling is clearer for users when using a separate “Unclassified” classification and the BSI/TISAX protection classes:
In our ISMS Blog: ISO/IEC 27001 — VDA ISA / TISAXyou will find the pictograms used for free use as well as further tips for your ISMS.
If you have any questions, please do not hesitate to contact us via our contact form any time.